Cybersecurity Website
Social Engineering
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. Unlike technical hacking, social engineering exploits human psychology rather than software or system vulnerabilities.
Common Social Engineering Tactics
- Pretexting: Creating a fabricated scenario to extract information or perform an action.
- Baiting: Offering something enticing to trick users into taking an action.
- Quid Pro Quo: Offering a service in exchange for information or access.
- Tailgating: Following someone into a restricted area without proper authorization.
- Scareware: Tricking users into thinking their device is infected to convince them to download malicious software.
Real-World Examples
- CEO Fraud: Impersonating executives to request urgent wire transfers or sensitive information.
- Tech Support Scams: Pretending to be from IT support to gain remote access to systems.
- Fake Job Offers: Creating fraudulent job listings to collect personal information.
- Impersonation: Pretending to be a trusted entity like a bank, government agency, or colleague.
Defending Against Social Engineering
- Verify requests for sensitive information through a different communication channel.
- Be skeptical of urgent requests, especially those involving financial transactions.
- Never provide credentials or personal information in response to an unsolicited request.
- Implement proper authentication procedures in organizations.
- Conduct regular security awareness training for all employees.
- Follow the principle of "trust but verify" for unusual requests.
Notable Social Engineering Attacks
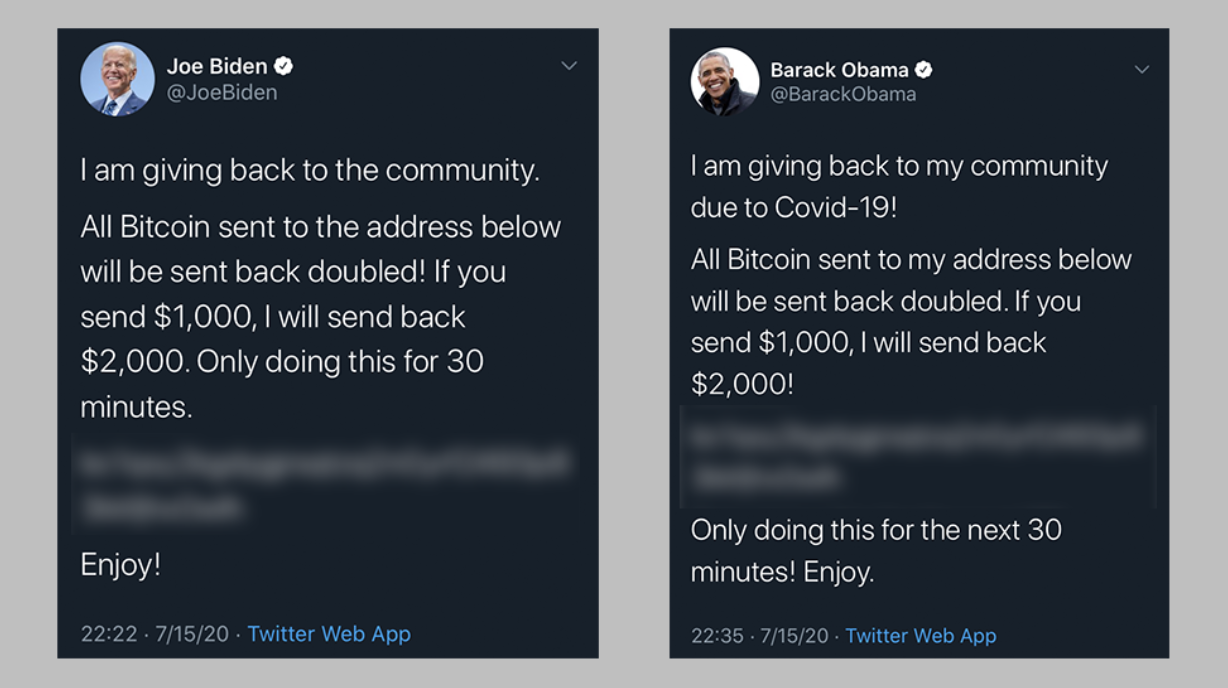
The Twitter Bitcoin Scam
2020A coordinated social engineering attack targeting Twitter employees, leading to the compromise of high-profile accounts to promote a Bitcoin scam.

The RSA SecurID Breach
2011Attackers used phishing emails to gain access to RSA's internal network, compromising the SecurID two-factor authentication system.